The TI & RT Procurement
Early in the Preparation phase the WT is supposed to procure TI and RT services.
The TI team will provide threat intel tailored to the CFI, whereas the Red Team will simulate the chosen threat actors’ modi operandi according to the TTI report.
Nevertheless, while thinking about prospective vendors you might bump into some dilemmas. Here is some.
By TIBER-EU process, the Scoping activities are set to be completed after the WT has concluded the procurement. Because of that, you better have an idea of the actual critical function to be tested, if not the full picture. You want to know what sort of skills and core competencies the vendors should have that matches the infrastructure that will be targeted and eventually tested.
In addition, your test project plan is supposed to be delivered after the vendors have been selected. However, the candidate vendors most likely will ask for dates they should commit on, by doing their own internal planning. Consequently, devise a draft project plan and discuss this with the TIBER Cyber Team before your RFP.
Procurement within TIBER-EU can vary depending on the size of your organization, nevertheless here is some advice on what to consider:
- Make sure the vendor you choose has an adequate size to withstand any sudden changes in the agreed allocated team (TI or RT)
- Ensure that you, as the WT, and your vendors interpret the TIBER- EU procurement requirements in a similar way. A difference in the requirements interpretation could incur significant differences in the offers cost
- Consider if you need the TI vendor during the RT phase to support in the RT Test plan development and advice during the test execution. If so, accommodate that in your contract terms with the TI vendor
- Consider if vendor local presence is important to you. If you choose global players, clarify early the legal aspects and implications. Don’t turn a red team exercise in a legal fight!
- Depending on your procurement process you want to allocate enough time for doing the right selection. Allocate at least 4 weeks to ensure a proper dialogue
TIBER Risk Management
Testing critical functions of your jurisdiction’s financial infrastructure indicates how important proper risk management activities are within TIBER-EU. Even though a standalone activity within the TIBER process, the WT should be dealing with risk management from beginning to end, as the risk picture is dynamic. Facilitate risk brainstorming sessions early in TIBER Initiation phase so that you know you are up against. In these sessions, invite both business and technical SME, if these profiles are included in your WT.
Here is some additional advice for dealing with identified risks:
- Assign a risk manager to facilitate the risk related activities, such as documentation, analysis, assessment, treatment and reporting
- Regularly revisit the open risks as the risk picture changes. Some risks are static, some other more volatile. See for instance the COVID19 related risks
- Make a risk assessment of the actual test scenarios and prepare your treatment plan
- When execution initiates, make short risk assessments of the upcoming RT planned activities. Make treatment decision according to you organization’s risk appetite and in alignment with your TIBER Cyber Team (TCT)
- Some of the risk information you might want to keep in your risk register is: Risk ID and type, source of the risk and its owner who will eventually need to approve the treatment actions
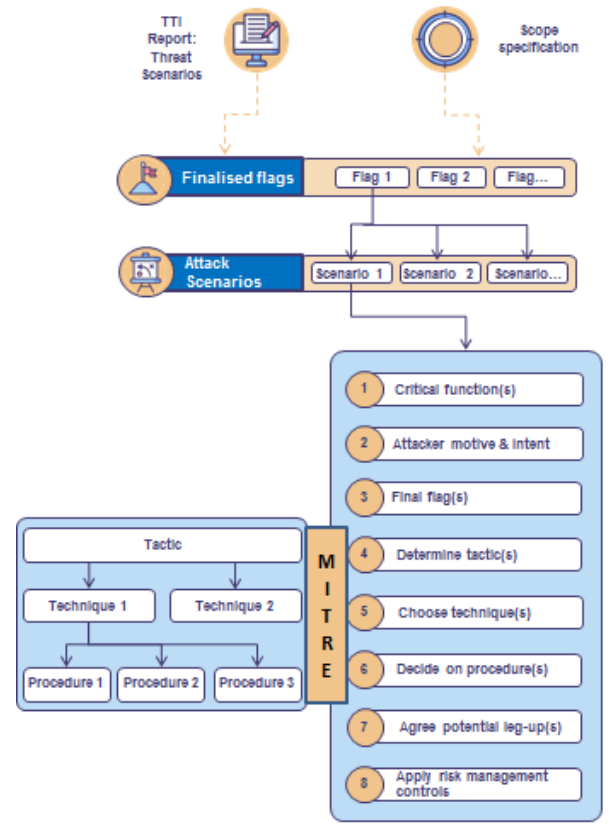
TIBER Scoping Activity
The key objective of this activity is to define the scope of the RT test. The scope must include the organization’s critical functions in terms of people, processes and technology. Note here that a critical function is not equal to a critical system. It is a function which could be considered critical or essential to the financial services sector and/or a financial services sector organization. For identifying your critical function, you can leverage, among others, business impact analyses, risk assessments and the EBA schemes which indicate systemic criticality.
By simply identifying the critical function to be tested, you are not done yet. The TIBER-EU Scope Specification template requires all sort of details, from underpinning critical systems, to flags that demonstrate compromise. Let’s see how you could do that:
- Once the critical function is identified, you identify also all underpinning systems, services or assets
- Afterwards you assign an information assurance threat category to the underpinning services. This category indicates what is your organization’s biggest concern in terms of Confidentiality, Integrity or Availability on a said service
- Then, in cooperation with the business you define a Compromise Action per service in scope. The Compromise Action relates to the assigned threat category and it describes shortly an adverse action against the service. You can think of a compromise actions as the “Actions on Objectives” in terms of the Cyber Kill Chain
- Final step is to set the flags or in other words the testing activity and goal required to demonstrate that the Compromise Action has been realized.
Even though, by TIBER-EU, the scope sign off comes at the end of the Preparation phase, you might want to initiate the scoping activities earlier in TIBER process, since the WT composition, the vendors procurement and risk management activities relate heavily with the result of the Scoping phase.
In the next and last post on TIBER-EU, I will focus on the Test Execution, WT success criteria and I will close with some piece of overall advice to the WT.

